Safeguard your business through a proven Risk Management Approach
Risk management has evolved into a well-recognised management discipline and is now considered key a governance and management tool within the public and private sectors.
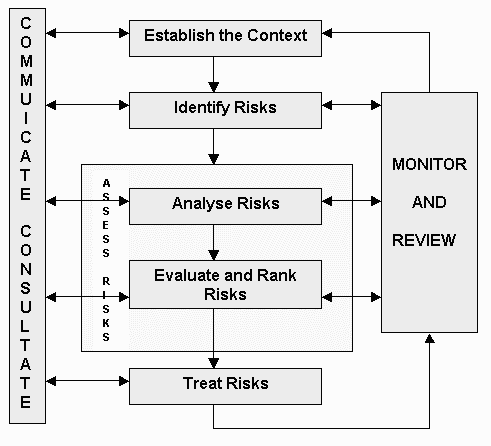
An effective risk management governance framework that allows for the identification and management of risks relating to a project is a critical process to understanding the likelihood of a successful outcome for any stakeholder deliverable. Our Risk Management Framework is consistent with AS/NZS ISO31000:2009.
Many organisations want to implement a more formal approach to managing risks to their business and developing a Risk Management Plan (RMP) is a good way to start things off. A RMP will usually describe in some detail how we will go about managing risks, who is involved in the process, and in what kind of formats will risk information be presented and managed.
The risk management process set out in the Standard is illustrated in the diagram.
The Need for Threat Risk Assessments
There is an emerging need for organisations to conduct Threat Risk Assessments (TRAs) on their Information and Communications Technology (ICT) infrastructure to identify and deal with threats to their critical systems.
There are many reasons besides simply good governance for undertaking a TRA. Among the most pressing motivations for conducting a TRA are:
- Businesses' heavy reliance on ICT and their networks;
- The potential for weaknesses in complex information networks in their design or implementation;
- The opportunity for risks to be avoided if they are identified early in design and development, avoiding costly remediation after systems are set to work;
- Certification of systems or networks containing sensitive or classified information may depend on completing a TRA; and
- Good governance requiring formal attention to threats to ICT infrastructure.
Information and Communications Technology Threats
We have found that most risks that arise can be grouped under a number of general headings, and that they evolve from a relatively common sets of threats.
While it is important to maintain an open mind and adopt an approach that will expose any new threats, we have found there to be a number of recurring threats, which include:
- The introduction of malicious code;
- Acts of terrorism;
- System hardware or software failure;
- Natural or environmental disasters;
- Attacks on the system by external networks or hackers;
- Eavesdropping on the system and;
- User-initiated issues, either through error or malicious acts.
We are finding that, as ICT systems become more complex and pervasive, new threats emerge. It is important that organisations remain vigilant to new threats and understanding how they may be affected.
The standard allows for a risk assessment process to be tailored to suit a specific activity. In the case of a TRA, we work with our clients to match the process to their unique requirements. Typically, this involves modifying scales of consequences and likelihood, introducing client-specific evaluation criteria, and adjusting the subsequent levels of risk severity. The result is a cost-effective process that is well matched to each ICT infrastructure requirement, and can be understood by all who participate in it and use its outcomes.